What is VeilNet? #
VeilNet is the world’s first Ephemeral Secure Network, unifying the strengths of Software-Defined Networking (SDN), The Onion Router (Tor), and Virtual Private Networks (VPN).
It provides the full usability of a Layer 3 network interface, like traditional VPNs, while offering the anonymity of the Tor network. VeilNet also implements the latest NIST FIPS 203 standard — ML-KEM (Module-Lattice-Based Key Encapsulation Mechanism) — delivering post-quantum cryptographic security. By leveraging SDN, it achieves optimal performance without the complexity of conventional routing protocols.
The structure of VeilNet #
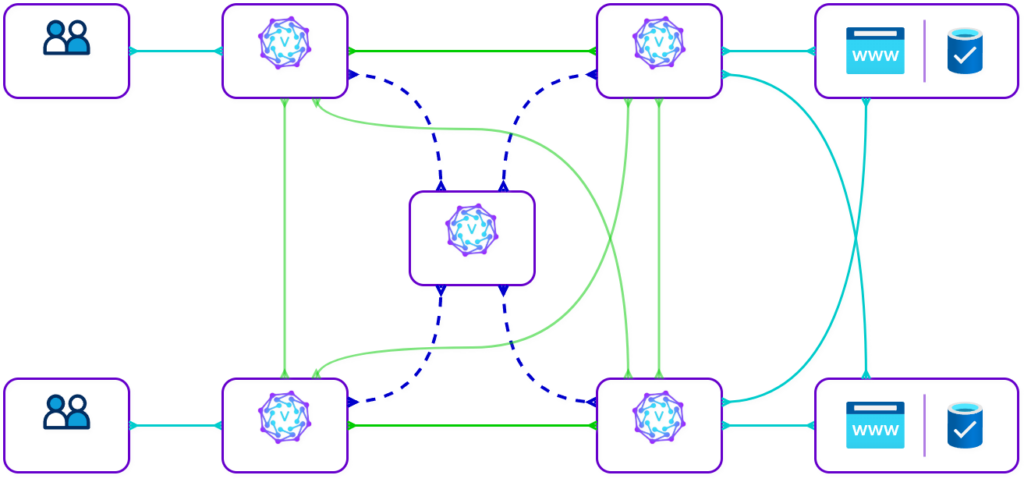
VeilNet features a fundamentally different architecture compared to conventional VPNs or even the Tor network. It functions more like a miniature internet, composed of two core layers. The first is a “local” or “access” network built on WireGuard tunnels — this is typically where traditional VPNs stop. Beyond that, VeilNet introduces a Tor-like “public network” layer, where all VeilNet Rifts can communicate. However, unlike Tor’s persistent circuits and routing tables, VeilNet uses ephemeral links that are created and torn down dynamically with the traffic itself, offering greater privacy, adaptability, and resilience.
How does routing in VeilNet works? #
VeilNet has solved one of the most enduring challenges in networking history — how to route packets reliably and efficiently when the network topology is unknown and constantly changing.
If you’re a networking professional, you might be asking: How is that even possible? After all, modern networking relies on well-established algorithms like Bellman-Ford in RIP (Routing Information Protocol), Dijkstra’s Algorithm in OSPF (Open Shortest Path First), and path vector algorithms in BGP and EIGRP. While these algorithms provide dynamic routing capabilities, their convergence times can range from several seconds to over 30 minutes under real-world conditions.
But what if the topology isn’t just changing — it’s ephemeral? What if links are created and destroyed in real time, along with the traffic itself?
In such conditions, conventional routing protocols become obsolete. They depend on persistent links, stable topology views, and precomputed routing tables — none of which apply in VeilNet’s environment.
To address this formidable challenge, VeilNet extends the principles of Software-Defined Networking (SDN) through a shared control and signaling channel known as the Veil Master. Unlike traditional SDN architectures that rely on a centralized controller with predefined logic, each VeilNet Rift operates autonomously, making real-time decisions using a priority-based algorithm inspired by Reinforcement Learning and Dynamic Programming.
In essence, every Rift acts as an AI-driven agent—independently evaluating its local context yet collaboratively working with others to forward traffic toward its destination with maximum speed and efficiency. This decentralized intelligence enables VeilNet to function without global topology awareness, dynamically adapting to changes in the network as they occur.
How does encryption work in VeilNet? #
VeilNet employs a multilayered encryption architecture that spans both symmetric and asymmetric cryptographic techniques, beginning the moment data leaves your device.
Before a packet can be transmitted, your Rift identifies the optimal peer Rift to forward the data toward its final destination outside VeilNet, establishing a logical peer-to-peer stream. A shared secret is generated and securely exchanged using ML-KEM, the most advanced post-quantum key exchange standard (FIPS 203). This secret forms the basis of an end-to-end encrypted channel.
Within your local access network, data is encrypted with ChaCha20 and authenticated via Poly1305, ensuring confidentiality even from others on the same physical network. Once the receiving Rift prepares the packet for transit across the VeilNet, it is re-encrypted using a unique stream encryption key specific to the destination.
From there, the packet travels through a series of ephemeral Rifts — with each hop dynamically chosen not just for anonymity, but also for optimal routing performance. These intermediate Rifts can relay the data, but cannot decrypt it. Only the source and destination Rifts share the key.
Moreover, the ephemeral links between Rifts apply an additional layer of asymmetric encryption, shielding metadata from surveillance by ISPs or network infrastructure providers.
At the destination Rift, the data is decrypted and forwarded as a standard IP packet, bearing a randomised private address assigned within VeilNet. If the destination is a local network, then the packet will be encrypted again via chacha20 & poly1305 to protect it within the target local network. There is no compromise to security or privacy — in fact, VeilNet’s ephemeral, encrypted fabric is so dynamic that even advanced intrusion detection tools or deep packet inspection will yield results that are incoherent and untraceable.

VeilNet isn’t just another privacy tool — it’s the future of secure communication. Built for a world where traditional networks fall short, VeilNet offers an ephemeral, AI-driven, post-quantum-secure architecture that renders surveillance obsolete and puts control back in your hands. Whether you’re an individual defending your privacy or an organization securing critical infrastructure, VeilNet adapts, encrypts, and protects — by design.
🚀 Join the movement.
Deploy a Rift. Join the community. Shape the network.
Explore the Community Tier today and become part of the most advanced privacy-preserving network ever built.



