What is Overlay VPN?
An overlay VPN is a type of virtual network built on top of the existing internet, designed to simplify connectivity between devices without requiring complex firewall or router configurations. Unlike traditional VPNs that rely on centralized servers, overlay VPNs create a secure mesh between endpoints, making devices feel like they are on the same local network even when they are physically scattered around the world.
Popular examples include Tailscale and Netbird. Both use the WireGuard protocol as their underlying encryption and tunneling layer, but add orchestration on top. Instead of manually setting up tunnels, these services provide a control plane that automatically manages peer discovery, key exchange, and routing. With just a client install and login, devices are enrolled into a private mesh network where they can securely communicate point-to-point, often bypassing NATs and firewalls without additional configuration.
Overlay VPNs are particularly attractive for remote teams and developers because they reduce the friction of secure access — no need to maintain complex VPN gateways or static infrastructure. However, since they still depend on WireGuard’s cryptographic suite and centralized coordination servers, their security and performance are ultimately limited by these design choices.
What is the downside of Overlay VPN?
While overlay VPNs like Tailscale and Netbird simplify private networking, they also come with important limitations.
-
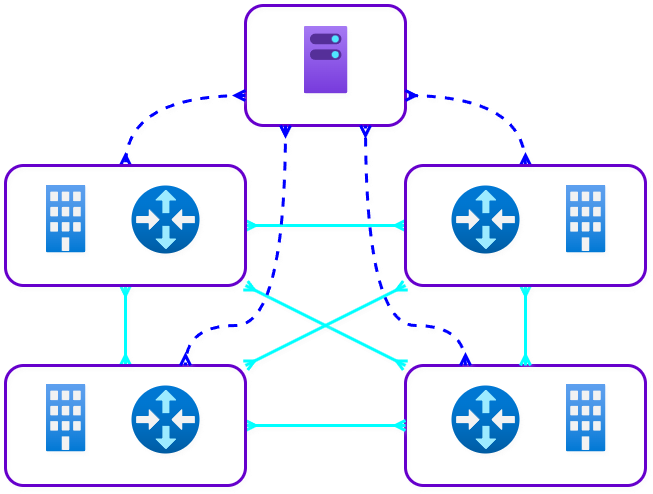
Key Storage and Coordination Servers
Overlay VPNs depend on a coordination server that stores each device’s public key and redistributes it to other peers. Although the traffic itself is end-to-end encrypted, the fact that a central authority holds the entire network’s key registry raises privacy and trust concerns. -
Enterprise-Oriented, Not Consumer-Friendly
These solutions are designed primarily for connecting sites, offices, and developer environments. They’re not built with consumer needs in mind, such as bypassing censorship, hiding traffic patterns, or scaling across millions of users. -
Dependence on Centralised Relay Servers
Overlay VPNs attempt direct peer-to-peer (P2P) links first. If that fails — for example, due to NAT or firewall restrictions — traffic is routed through a centralised relay server operated by the provider. If that relay server is blocked or fails, the connection simply stops working, because other peers in the network cannot step in to act as relays. This creates a single point of failure that undermines the resilience of the system. -
Poor Scalability
The mesh design means that the number of connections grows exponentially with the number of devices. In practice, this becomes inefficient and difficult to manage beyond a certain scale. Even enterprises that adopt overlay VPNs often still maintain a traditional VPN to serve regular users, because the mesh cannot scale to thousands or millions of endpoints.
As evidence of this limitation, all major overlay VPN providers — including Tailscale and Netbird — charge based on the number of devices connected to the network. This pricing model reflects the fact that device count directly drives complexity and load in a mesh, making scalability costly.
How does VeilNet address the downsides of Overlay VPN?
VeilNet was designed with a different philosophy from overlay VPNs like Tailscale or Netbird. Instead of relying on centralised coordination or fragile mesh topologies, VeilNet builds a post-quantum, decentralised network that solves the shortcomings of existing approaches.
-
No Centralised Key Registry
VeilNet does not rely on a central server to store or redistribute keys. Instead, key exchange happens directly between peers via an isolated control channel, using Kyber KEM for post-quantum key exchange and Dilithium DSA for digital signatures, paired with AES-256 GCM for encryption. There is no central database or server that ever holds this information, which eliminates the risks of centralised trust. -
Built for Both Consumers and Enterprises
Unlike overlay VPNs, which are tailored for site-to-site enterprise networking, VeilNet is equally suitable for individual consumers and large organisations. Consumers gain unblockable privacy and censorship resistance, while enterprises gain post-quantum security, scalability, and decentralised reliability — all on the same platform. -
Decentralised Relaying Instead of Centralised Servers
If a direct peer-to-peer link fails, VeilNet doesn’t fall back to a single provider-owned relay. Instead, any other node in the network can step in as a relay, automatically selected by a reinforcement learning algorithm that evaluates conditions in real time. This removes the single point of failure found in overlay VPNs and ensures that connections stay alive, even in restrictive environments. -
Scalable by Design
VeilNet does not rely on full-mesh connectivity, which grows exponentially with the number of devices. Instead, it uses on-demand ephemeral channels that are created only when needed and destroyed once idle, with traffic balanced intelligently across the network. This makes the system inherently scalable — more users mean more nodes, more links, and better performance.
Because of this architecture, VeilNet doesn’t need to charge per device. The network actually becomes faster and more resilient as it grows, in sharp contrast to overlay VPNs that slow down and become more costly to maintain with each additional endpoint.

